Keep Your Old Phone: Adding Failover to Your Life
If you're upgrading to a new phone, don't throw your old one away. Keep it.
Written by Allen Liu, Self-published 2024 - 05 - 19
To include the boring personal parts, click here.
Recently, I damaged my Pixel 7. I'm extremely embarassed about it now because I knew better and I knew I knew better, but I did it anyway: I washed my phone with soap and water. I thought I was careful by avoiding the charging port, but water resistance can only go so far. And it had worked in the past, where I had washed my phone with soap and water and suffered no real consequences. It was something I just did, even though I knew better and knew I knew better. I had even bought a sprayer for rubbing alcohol to avoid this situation, but I kept misplacing it and didn't feel like trying to find it. I took it down to a repair shop and had it fixed, and it took just over a week for the parts to arrive and repairs to happen. I finally got it back after over a wek, but it still had issues with receiving calls, so I wanted to get the SIM card replaced. Then I flew back home and less than two weeks after getting my phone back, I did it again. I washed my phone with soap and water again, this time with another excuse that it was because I had gotten pesticide on it. In hindsight, 70% alcohol would've done the job just as well, but that's what I get for not learning my lesson. I'm still embarassed telling this story I shouldn't need to tell, but there was a lesson I could actually take away from it.
There are several fundamental acronyms in cybersecurity, and one of them is the CIA triad: confidentiality, integrity, and accessibility. In cybersecurity, we're mostly focused on ways to narrow down accessibility and integrity to an acceptible level while maximizing confidentiality. Setting up access controls is one example, where access controls preserve accessibility to data for management and accounting while increasing confidentiality by preventing unauthorized users from accessing said data. The drawback is this does reduce accessibility and can lead to organizational friction, where lower level employees are prohibited from accessing ertain data without asking upper level management.
This is usually considered an acceptable tradeoff or even a good thing, as sensitive corporate documents such as trade secrets shouldn't be open to lower level employees who aren't directly incentivized to stay. But this does make access harder to manage, as access controls can sometimes be more difficult to explain or justify to laypersons. Additionally, in smaller organizations, some very sensitive corporate documents may only have one or two accounts that can even see the data. If those accounts are to be compromised and the data is deleted or ransomed, no other users would have been able to hold backup copies, and the data may be lost forever. This is where accessibility comes in, and where redundancy and failover enter our picture.
Redundancy and failover go hand in hand in cybersecurity, but they're not the same thing. Failover is the ability to automatically recover from failure, but it often is implemented with redundancy, by having redundant systems in place to keep up the load to help with failover. As an example, many businesses will load balance their web servers with a second identical virtual machine running the same software that can boot up should the main server fail or need maintenance.
But what's sometimes lost in abstraction here is that a redundant system doesn't have to be a full copy, it just has to be enough to keep the lights on. A grocery store's redundant generator doesn't have to replace the entire power grid, but it should keep the refridgerators and cash registers running. If you're upgrading to a new phone, don't throw your old one away. Keep it.
With the rise of 2FA and MFA, phones have become more and more integral to our regular lives. Most workplaces will ask you to set up MFA through Duo Mobile, Microsoft Authenticator, Google Authenticator, or some other service, and most of these require you to have your exact phone. You may remember that around the mid 2010s, it was more common for apps to send two-factor authentication codes through SMS. If you lost your phone, you could still request a new SIM card or setup a Google Voice number to accept texts instead. These options still work today, but today's 2FA suite of authenticator apps are configured to your phone's exact hardware. As such, if you lose your phone, you lose access to your account.
But there are ways of mitigating this damage. Here, we can apply the concept of failover. If you have your old phone, here are some steps you can take.
If your old phone has some damage or is unusable, it may be worth taking it to a repair shop and determining how much it would cost to fix it. It's up to you to decide exactly what price you're willing to pay, but if you only need a screen replacement or similar, it may be worth it to pay. These steps assume your phone is at least in a usable state, even if degraded.
Click here for steps for transferring Google Authenticator.
These steps assume you are transferring your credentials from your old phone to your new phone. If you are doing the reverse, click here.
- Open Google Authenticator on your old phone.
- On your old phone, open the menu and select Transfer accounts.
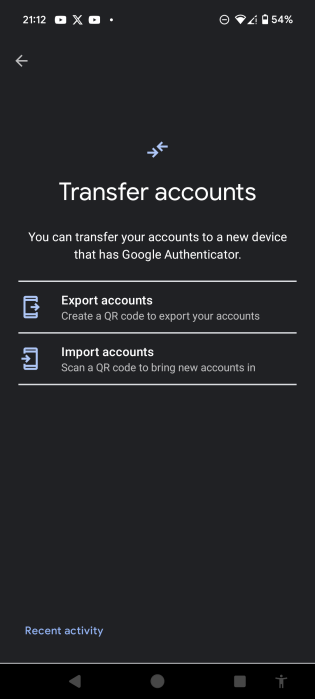
- On your old phone, select Export accounts.
- On your old phone, authenticate using PIN, thumbprint, face ID, etc.
- If desired, select which accounts to transfer and not to transfer. Otherwise, transfer all.
- On your old phone, select Next. A QR code should appear on screen.

- Open Google Authenticator on your new phone.
- On your new phone, open the menu and select Transfer acounts.

- On your new phone, select Import accounts.
- On your new phone, click Scan QR code.
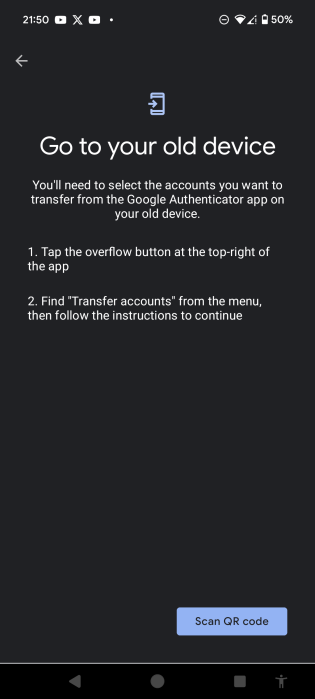
- On your new phone, scan your old phone's QR code.
- If prompted, use the Next button on your old phone to view the next QR code.

- On your new phone, scan your old phone's new QR code.
- Repeat steps 12-13 as necessary.
- Verify that all codes on both phones are identical.
Click here for steps for transferring Microsoft Authenticator.
Click here for steps for transferring Duo.



